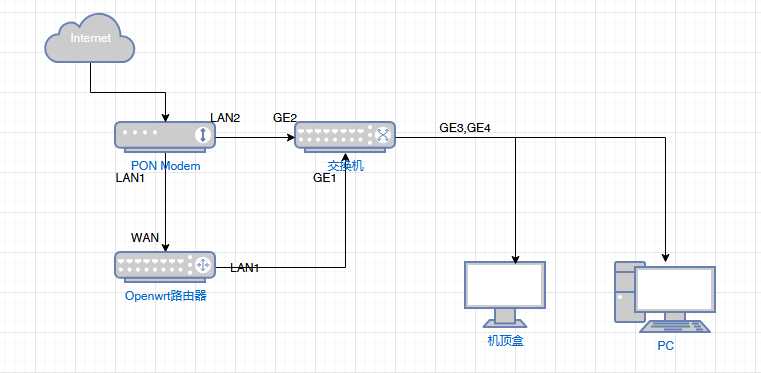
Machine Learning vs Artificial Intelligence: Whats the Difference?

The existence of current AI/ML capabilities does not mean a private equity firm will not have to invest significantly in improving AI/ML, particularly if the training datasets will need to be overhauled post-close. Developed by OpenAI, GPT-4 is one of the largest publicly available LLM models. It has been trained on a large amount of data and has higher accuracy and ability to generate text than previous models.
Yet, their intricate interplay and unique characteristics often spark confusion. In this article, we embark on a journey to demystify the trio, exploring the fundamental differences and symbiotic relationships between ML vs DL vs AI. Unravel the intricacies of each domain and gain a comprehensive understanding of how these transformative technologies collectively shape the future of intelligent systems and drive unparalleled advancements in our digital landscape.

An alternative is to discover such features or representations through examination, without relying on explicit algorithms. They let the machines learn independently, ingesting https://chat.openai.com/ vast amounts of labeled data and unlabeled data to detect patterns. Advancements in big data and the vast data we have collected enabled machine learning in the first place.
Learning in ML refers to a machine’s ability to learn based on data and an ML algorithm’s ability to train a model, evaluate its performance or accuracy, and then make predictions. This subcategory of AI uses algorithms to automatically learn insights and recognize patterns from data, applying that learning to make increasingly better decisions. Reinforcement learning is the most complex of these three algorithms in that there is no data set provided to train the machine. Instead, the agent learns by interacting with the environment in which it is placed. It receives positive or negative rewards based on the actions it takes, and improves over time by refining its responses to maximize positive rewards.
What is artificial intelligence (AI)?
As AI/ML continues to grow in value and capability, consistent leading practices for compliance and data management must factor into growth plans through an end-to-end AI/ML due diligence framework. In light of anticipated changes in legal and compliance regulations, private equity firms should adopt a rigorous end-to-end assessment as a key best practice to ensure they remain in compliance with the new requirements. The relative “newness” of AI/ML for most private equity firms means there is a lot of confirmation bias around AI/ML capabilities.
A. AI and ML are interconnected, with AI being the broader field and ML being a subset. Through integrating the Epicor Catalog–a comprehensive, cloud-based database with access to over 17 million SKUs from 9,500+ manufacturers– Carvana has dramatically increased productivity and cut the cost per unit for parts by more than 50%. Many companies have successfully integrated Epicor’s AI and ML solutions for a remarkable transformation in their business operations. Despite their prevalence in everyday activities, these two distinct technologies are often misunderstood and many people use these terms interchangeably.
Large language models serve as foundation models, providing a basis for a wide range of natural language processing (NLP) tasks. Generative AI can encompass a range of tasks beyond language generation, including image and video generation, music composition, and more. Large language models, as one specific application of generative AI, are specifically designed for tasks revolving around natural language generation and comprehension.

So now you have a basic idea of what machine learning is, how is it different to that of AI? We spoke to Intel’s Nidhi Chappell, head of machine learning to clear this up. For example, suppose you were searching for ‘WIRED’ on Google but accidentally typed ‘Wored’. After the search, you’d probably realise you typed it wrong and you’d go back and search for ‘WIRED’ a couple of seconds later. Google’s algorithm recognises that you searched for something a couple of seconds after searching something else, and it keeps this in mind for future users who make a similar typing mistake.
Specific practical applications of AI include modern web search engines, personal assistant programs that understand spoken language, self-driving vehicles and recommendation engines, such as those used by Spotify and Netflix. The system used reinforcement learning to learn when to attempt an answer (or question, as it were), which square to select on the board, and how much to wager—especially on daily doubles. Explore the benefits of generative AI and ML and learn how to confidently incorporate these technologies into your business. Ensure that team members can easily share knowledge and resources to establish consistent workflows and best practices. For example, implement tools for collaboration, version control and project management, such as Git and Jira. In its most complex form, the AI would traverse several decision branches and find the one with the best results.
Further Differences Between AI and Machine Learning
In this blog post, we may have used or referred to third party generative AI tools, which are owned and operated by their respective owners. Elastic does not have any control over the third party tools and we have no responsibility or liability for their content, operation or use, nor for any loss or damage that may arise from your use of such tools. Please exercise caution when using AI tools with personal, sensitive or confidential information. There is no guarantee that information you provide will be kept secure or confidential. You should familiarize yourself with the privacy practices and terms of use of any generative AI tools prior to use.
AWS offers a wide range of services to help you build, run, and integrate artificial intelligence and machine learning (AI/ML) solutions of any size, complexity, or use case. To paraphrase Andrew Ng, the chief scientist of China’s major search engine Baidu, co-founder of Coursera, and one of the leaders of the Google Brain Project, if a deep learning algorithm is a rocket engine, data is the fuel. Unlike machine learning, deep learning uses a multi-layered structure of algorithms called the neural network.
Even though we talked about machine learning being more limited in scope, it does make it possible for AI tools to solve and address varied problems across different sectors. Machine learning is behind many of these applications, making it possible for AI to be so dynamic. For AI, you can use AWS services to build your own AI solutions from scratch or integrate prebuilt artificial intelligence (AI) services into your solution. ML is best for identifying patterns in large sets of data to solve specific problems.
But while AI and machine learning are very much related, they are not quite the same thing. The intention of ML is to enable machines to learn by themselves using data and finally make accurate predictions. We’re the world’s leading provider of enterprise open source solutions—including Linux, cloud, container, and Kubernetes. We deliver hardened solutions that make it easier for enterprises to work across platforms and environments, from the core datacenter to the network edge.

Machine learning also incorporates classical algorithms for various kinds of tasks such as clustering, regression or classification. The more data you provide for your algorithm, the better your model and desired outcome gets. Machine learning is a relatively old field and incorporates methods and algorithms that have been Chat GPT around for dozens of years, some of them since the 1960s. These classic algorithms include the Naïve Bayes classifier and support vector machines, both of which are often used in data classification. In addition to classification, there are also cluster analysis algorithms such as K-means and tree-based clustering.
Getting started in AI and machine learning
This stems from the technology using existing content to inform how it creates its own “original” content. As the AI field continues to grow, questions will continue to be asked about its ethics, and it will be a challenge in its own right to decide on and enforce ways to keep everyone safe. You can infer relevant conclusions to drive strategy by correctly applying and evaluating observed experiences using machine learning. While we are not in the era of strong AI just yet—the point in time when AI exhibits consciousness, intelligence, emotions, and self-awareness—we are getting close to when AI could mimic human behaviors soon. We can compare the model’s prediction with the ground truth value and adjust the parameters of the model so next time the error between these two values is smaller.
While ML is a powerful tool for solving problems, improving business operations and automating tasks, it’s also complex and resource-intensive, requiring deep expertise and significant data and infrastructure. You can foun additiona information about ai customer service and artificial intelligence and NLP. Choosing the right algorithm for a task calls for a strong grasp of mathematics and statistics. Training ML algorithms often demands large amounts of high-quality data to produce accurate results. The results themselves, particularly those from complex algorithms such as deep neural networks, can be difficult to understand. Semi-supervised anomaly detection techniques construct a model representing normal behavior from a given normal training data set and then test the likelihood of a test instance to be generated by the model.
Though used interchangeably, here’s the real difference between artificial intelligence vs. machine learning vs. deep learning. Artificial intelligence performs tasks that require human intelligence such as thinking, reasoning, learning from experience, and most importantly, making its own decisions. As our article on deep learning explains, deep learning is a subset of machine learning.

Many algorithms and techniques aren’t limited to a single type of ML; they can be adapted to multiple types depending on the problem and data set. For instance, deep learning algorithms such as convolutional and recurrent neural networks are used in supervised, unsupervised and reinforcement learning tasks, based on the specific problem and data availability. Machine Learning and Artificial Intelligence are two closely related but distinct fields within the broader field of computer science. It involves the development of algorithms and systems that can reason, learn, and make decisions based on input data.
Machine learning vs. deep learning neural networks
Similarly, decision-making and predictions are both key parts of nearly all AI tools. This is because assessing information, weighing up options, and deciding the best next step is an integral part of any intelligence. The machine learning algorithms analyze huge amounts of data to identify the patterns that facilitate this decision-making. AI’s primary goal is to mimic human intelligence and abilities, such as reasoning, decision-making, and adaptability. It achieves this with a combination of techniques, but the most critical method is almost always machine learning.
That’s because these machine learning algorithms make it possible for the AI to analyze information, identify patterns, and adapt its behavior. Artificial intelligence (AI) is an umbrella term for different strategies and techniques you can use to make machines more humanlike. AI includes everything from smart assistants like Alexa to robotic vacuum cleaners and self-driving cars.
- So now you have a basic idea of what machine learning is, how is it different to that of AI?
- Artificial intelligence (AI) describes a machine’s ability to mimic human cognitive functions, such as learning, reasoning and problem solving.
- This is because assessing information, weighing up options, and deciding the best next step is an integral part of any intelligence.
- The problem is that these situations all required a certain level of control.
The broader aim of AI is to create applications and machines that can simulate human intelligence to perform tasks, whereas machine learning focuses on the ability to learn from existing data using algorithms as part of the wider AI goal. Today, artificial intelligence is at the heart of many technologies we use, including smart devices and voice assistants such as Siri on Apple devices. In simplest terms, AI is computer software that mimics the ways that humans think in order to perform complex tasks, such as analyzing, reasoning, and learning. Machine learning, meanwhile, is a subset of AI that uses algorithms trained on data to produce models that can perform such complex tasks. DL is able to do this through the layered algorithms that together make up what’s referred to as an artificial neural network. These are inspired by the neural networks of the human brain, but obviously fall far short of achieving that level of sophistication.
Unsupervised machine learning
We define weak AI by its ability to complete a specific task, like winning a chess game or identifying a particular individual in a series of photos. Natural language processing and computer vision, which let companies automate tasks and underpin chatbots and virtual assistants such as Siri and Alexa, are examples of ANI. Many people use machine learning and artificial intelligence interchangeably, but the terms have meaningful differences. As the quantity of data financial institutions have to deal with continues to grow, the capabilities of machine learning are expected to make fraud detection models more robust, and to help optimize bank service processing. As outlined above, there are four types of AI, including two that are purely theoretical at this point.
Implementing quality management systems to close the AI translation gap and facilitate safe, ethical, and effective health AI solutions npj Digital Medicine – Nature.com
Implementing quality management systems to close the AI translation gap and facilitate safe, ethical, and effective health AI solutions npj Digital Medicine.
Posted: Sat, 25 Nov 2023 08:00:00 GMT [source]
For example, you can train a system with supervised machine learning algorithms such as Random Forest and Decision Trees. Data management is more than merely building the models that you use for your business. You need a place to store your data and mechanisms for cleaning it and controlling for bias before you can start building anything.
Principal component analysis (PCA) and singular value decomposition (SVD) are two common approaches for this. Other algorithms used in unsupervised learning include neural networks, k-means clustering, and probabilistic clustering methods. Machine learning is a form of artificial intelligence (AI) that can adapt to a wide range of inputs, including large data sets and human instruction. The algorithms also adapt in response to new data and experiences to improve over time.
In the real world, the terms framework and library are often used somewhat interchangeably. But strictly speaking, a framework is a comprehensive environment with high-level tools and resources for building and managing ML applications, whereas a library is a collection of reusable code for particular ML tasks. Reinforcement learning involves programming an algorithm with a distinct goal and a set of rules to follow in achieving that goal. The algorithm seeks positive rewards for performing actions that move it closer to its goal and avoids punishments for performing actions that move it further from the goal.
While artificial intelligence (AI), machine learning (ML), deep learning and neural networks are related technologies, the terms are often used interchangeably, which frequently leads to confusion about their differences. Deep learning is a subset of machine learning that uses several layers within neural networks to do some of the most complex ML tasks without any human intervention. As with the different types of AI, these different types of machine learning cover a range of complexity. And while there are several other types of machine learning algorithms, most are a combination of—or based on—these primary three. Toloka is a European company based in Amsterdam, the Netherlands that provides data for Generative AI development. We are the trusted data partner for all stages of AI development from training to evaluation.
The Meaning of Explainability for AI – Towards Data Science
The Meaning of Explainability for AI.
Posted: Mon, 03 Jun 2024 07:00:00 GMT [source]
Oracle Cloud Infrastructure (OCI) provides the foundation for cloud-based data management powered by AI and ML. The field of AI encompasses a variety of methods used to solve diverse problems. These methods include genetic algorithms, neural networks, deep learning, search algorithms, rule-based systems, and machine learning itself. Inspired by DevOps and GitOps principles, MLOps seeks to establish a continuous evolution for integrating ML models into software development processes. By adopting MLOps, data scientists, engineers and IT teams can synchronously ensure that machine learning models stay accurate and up to date by streamlining the iterative training loop.
Developers filled out the knowledge base with facts, and the inference engine then queried those facts to get results. Reinforcement learning is often used to create algorithms that must effectively make sequences of decisions or actions to achieve their aims, such as playing a game or summarizing an entire text. In this article, you’ll learn more about what machine learning is, including how it works, different types of it, and how ml and ai meaning it’s actually used in the real world. We’ll take a look at the benefits and dangers that machine learning poses, and in the end, you’ll find some cost-effective, flexible courses that can help you learn even more about machine learning. But still, there lack datasets with a great density that be used for testing AI algorithms. For instance, the standard dataset used for testing the AI-based recommendation system is 97% sparse.
Views: 3