- 通过命令配置nft
nft add chain inet fw4 gfw_prerouting { type filter hook prerouting priority mangle\; policy accept\; } nft add chain inet fw4 gfw_output { type route hook output priority mangle\; policy accept\; } nft add rule inet fw4 gfw_prerouting ip daddr @GFWLIST counter ct mark set 0x10 nft add rule inet fw4 gfw_prerouting ip daddr @GFWLIST counter meta mark set ct mark nft add rule inet fw4 gfw_output ip daddr @GFWLIST counter ct mark set 0x10 nft add rule inet fw4 gfw_output ip daddr @GFWLIST counter meta mark set ct mark以上gfw_output链处理本地发现的包,gfw_prerouting处理转发的包,在foward链中处理mark是不生效的(所以无法用uci配置)。
-
通过配置文件配置nft
创建文件/etc/nftables.d/11-gfw.nft
文件内容:chain gfw_forward { type filter hook prerouting priority mangle; policy accept; ip daddr @GFWLIST counter ct mark set 0x10 ip daddr @GFWLIST counter meta mark set ct mark } chain gfw_output { type route hook output priority mangle; policy accept; ip daddr @GFWLIST counter ct mark set 0x10 ip daddr @GFWLIST counter meta mark set ct mark }service firewall restart
这里要注意的是output hook只能是rotue链,不能是filter链,而prerouting则只能是filter链 - 添加策略路由匹配mark
ip rule add fwmark 0x10 table 50
这条策略路由是可以从界面上添加的
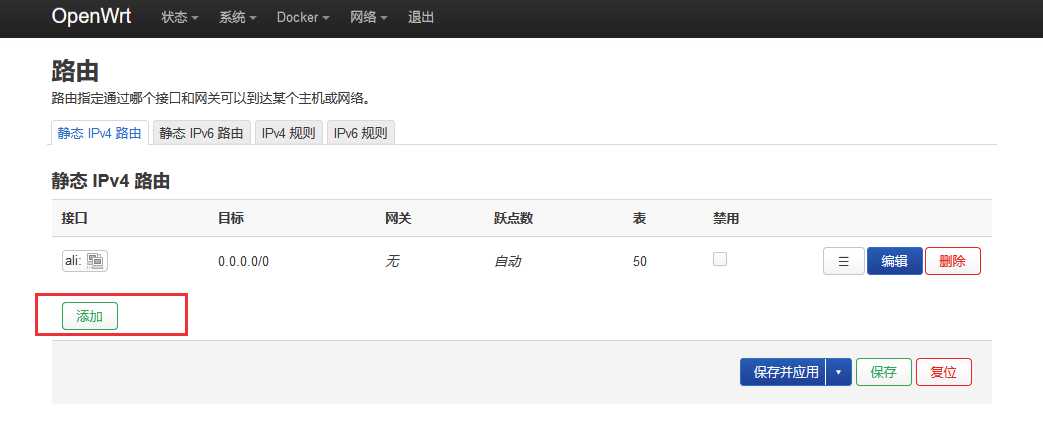
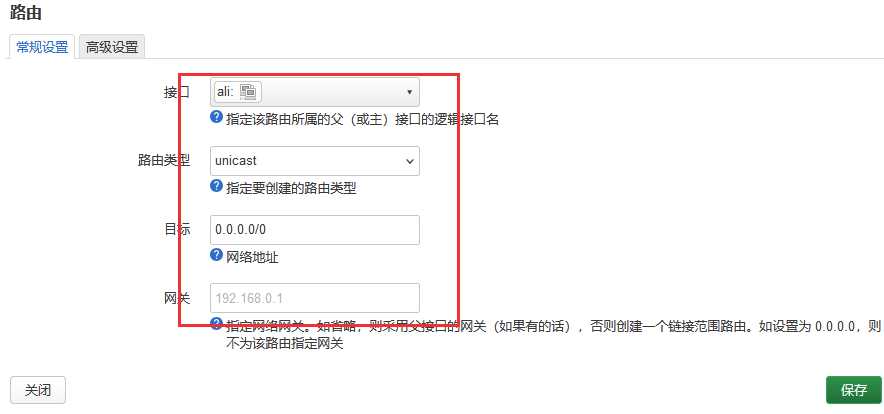
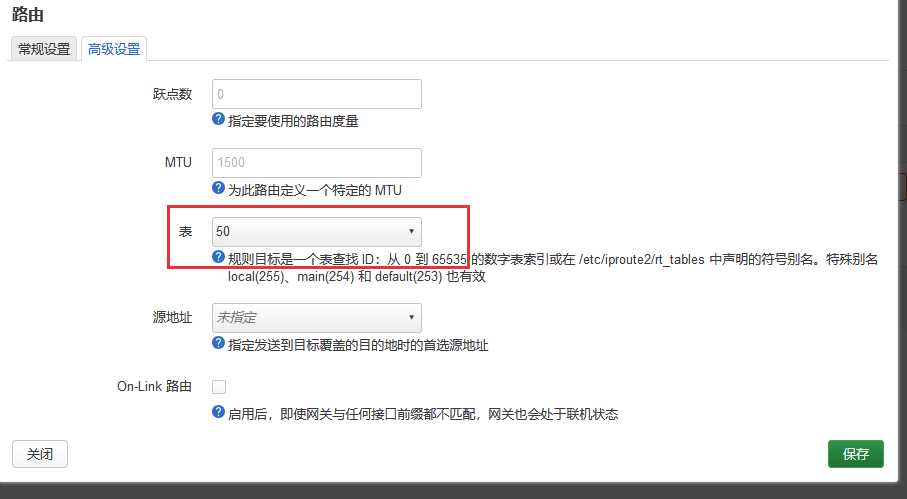
界面配置略繁锁一些。
Views: 26