- 密钥层次

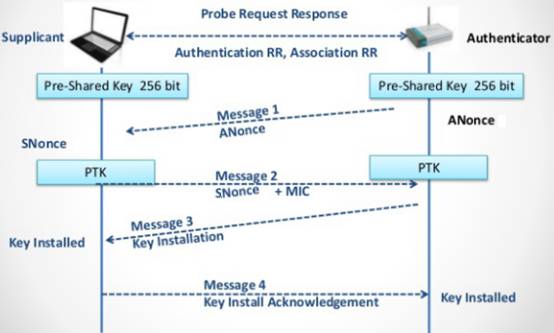
- 握手过程
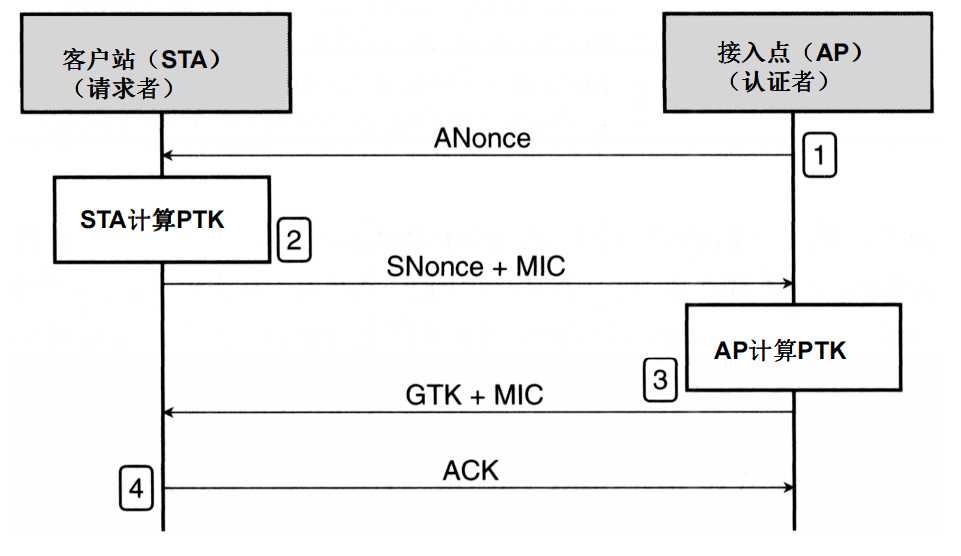
握手过程是通过EAPOL报文封装的,也可以称为EAPOL握手。 - 完整的连接过程

- KRACK
诱导AP重发Message3报文可以让STA重装PTK密钥,重装密钥的同时初始化向量会重新计数,造成加密密钥重复使用。
在STA上重装相同的密钥并不是802.11规定的,是认证客户端在实现的时候(wpa_supplicant2.4以下版本)没有意思到密钥重装会带来安全问题,当然802.11也没有提醒这一点。
KRACK解决方法: - 在STA上一次EAPOL握手只允许安装一次PTK密钥,禁止密钥重装
- STA安装密钥时判断与现有密钥是否相同,相同则忽略当前密钥安装
- 禁止或限制AP重发Message 3报文
完全禁止重发Message 3会对连接稳定性造成影响,目前一般是在AP上限制重发次数(通常是3或4次)并在 STA上禁止密钥重装。
Openwrt或hostapd上有一个禁止重发Message1和Message3报文的配置
# Workaround for key reinstallation attacks
#
# This parameter can be used to disable retransmission of EAPOL-Key frames that
# are used to install keys (EAPOL-Key message 3/4 and group message 1/2). This
# is similar to setting wpa_group_update_count=1 and
# wpa_pairwise_update_count=1, but with no impact to message 1/4 and with
# extended timeout on the response to avoid causing issues with stations that
# may use aggressive power saving have very long time in replying to the
# EAPOL-Key messages.
#
# This option can be used to work around key reinstallation attacks on the
# station (supplicant) side in cases those station devices cannot be updated
# for some reason. By removing the retransmissions the attacker cannot cause
# key reinstallation with a delayed frame transmission. This is related to the
# station side vulnerabilities CVE-2017-13077, CVE-2017-13078, CVE-2017-13079,
# CVE-2017-13080, and CVE-2017-13081.
#
# This workaround might cause interoperability issues and reduced robustness of
# key negotiation especially in environments with heavy traffic load due to the
# number of attempts to perform the key exchange is reduced significantly. As
# such, this workaround is disabled by default (unless overridden in build
# configuration). To enable this, set the parameter to 1.
#wpa_disable_eapol_key_retries=1
Views: 54

发表回复
要发表评论,您必须先登录。